From a user perspective, signing onto the internet is so straightforward that most people don’t even
question it. When your computer or mobile device connects to the internet, the process of logging onto
the network and obtaining your unique internet address for sending and receiving data is all thanks to
something called the internet protocol suite. How to Mitigate TCP Syn Flood Attacks?
Of this set of protocols, among the most critical is the transmission Control Protocol (TCP), the internet standard when it comes to the successful exchanging of data packets over a network. Whether it’s email applications, peer-to-peer apps, FTP, or web servers
and websites, the TCP protocol is what makes everything possible when it comes to online communication.
To work, a TCP connection needs to make what is referred to as a three-way handshake, involving both
the client and the server. To begin the handshake, the client sends the server an SYN packet connection
request. The server then answers with an SYN/ACK packet, which acknowledges the connection request
has been made. As the last step, the client — having received the SYN/ACK packet — responds with an
ACK packet.
This process is technically referred to as the SYN, SYN-ACK, ACK sequence. The three-way
handshake might sound like a simple greeting (a bit like saying “hello” to a buddy, getting a “hey!” back,
and then responding with another message to confirm that you were initiating a conversation), but it’s
an important interaction — not least because it adds an element of security that protects against
spoofing.
TCP has its weaknesses
Source: amazonaws.com
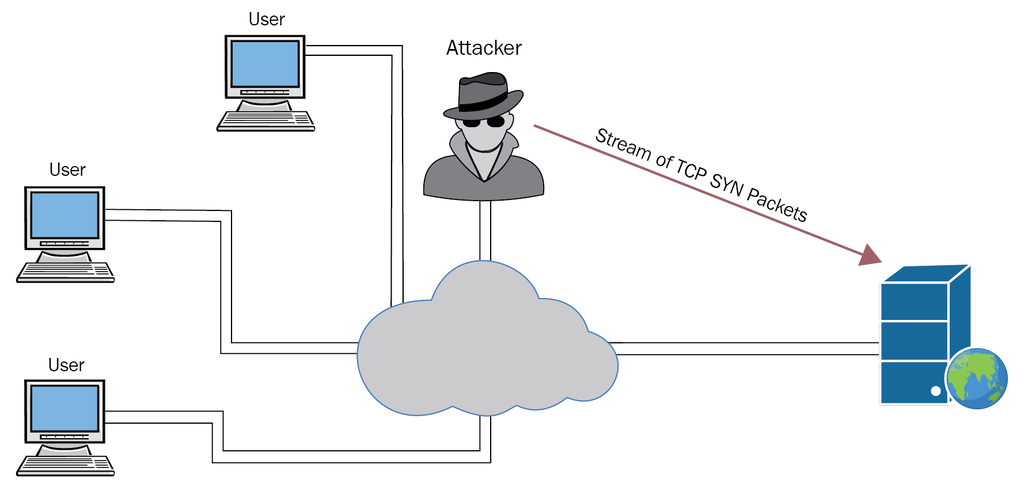
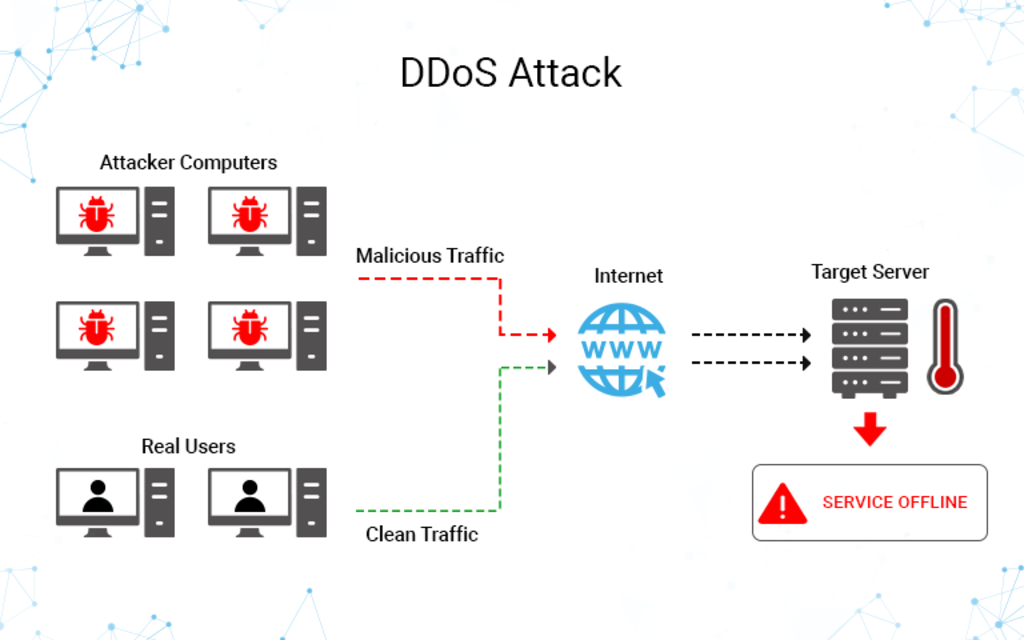
But TCP isn’t infallible. It’s vulnerable to several types of DDoS (distributed denial of service) attacks. The
most common of these is an SYN flood. In a DDoS attack, the attacker targets the victim with large
quantities of junk traffic with the aim of overwhelming their system and causing it to become
inaccessible to legitimate traffic.
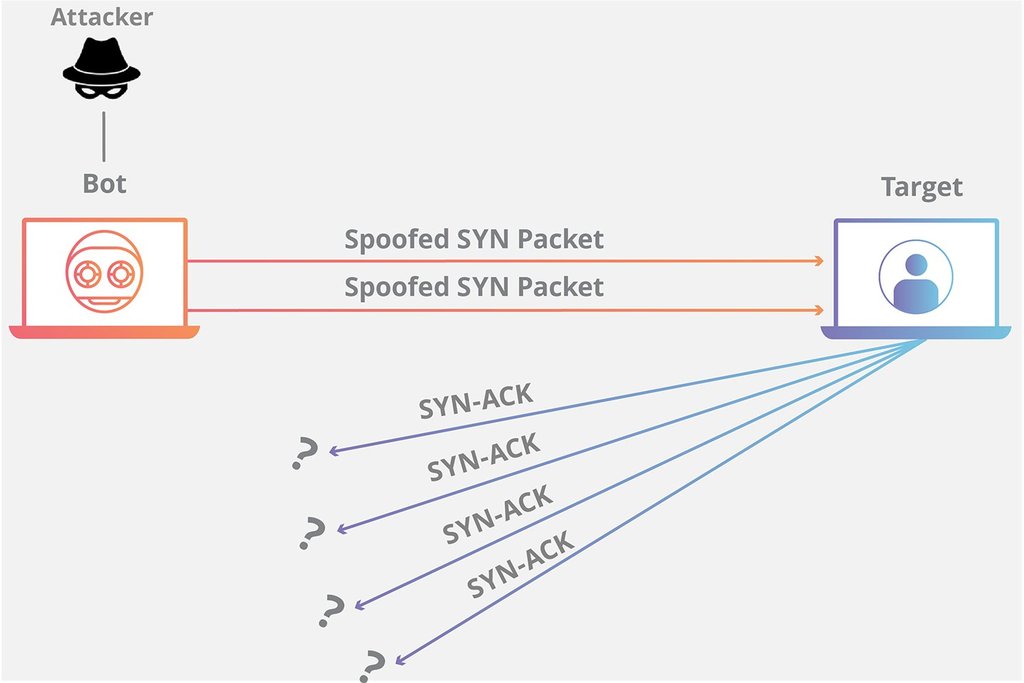
An SYN flood takes place during the three-way handshake process described above. The difference is that, unlike a normal SYN, SYN-ACK, ACK sequence, in an SYN flood attack these “hello” requests are sent by the attacker to every port on a victim’s machine at a rate that is faster than it’s able to process.
Overloaded by trying to process too many fake SYN requests at once, the machine stops being able to respond to legitimate TCP requests. This type of attack is also known as a TCP State-Exhaustion Attack. While the premise of the attack might sound simple, an SYN flood can
bring even the highest capacity devices, capable of millions of connections, to a standstill.
While an SYN flood counts as a DDoS attack, it is different in one keyway. A regular DDoS attack aims to
use up a target’s memory. An SYN flood instead works by overloading the open connections that are
connected to a port.
Every time an SYN packet connection request is made, the TCP goes into a “listen”
state. Exploiting this behavior, the SYN flood causes the host to enter this state, responding to fake half-
connections, until it has no resources left. SYN floods are sometimes referred to as “half-open” attacks
for this reason.
Defending against SYN flood vulnerabilities
Source: cloudflare.com
The vulnerability that could lead to a TCP SYN flood was first discovered as far back as 1994 by security
researchers Bill Cheswick and Steve Bellovin. At the time, there was no existing countermeasure that
could protect against such an attack. Fortunately, things have advanced in the years since. Several
methods of mitigating SYN floods now exist.
One such example is an SYN cookie, in which the server utilizes cryptographic hashing in order to confirm
as legitimate a TCP request before allotting any memory to it. With an SYN cookie, the recipient responds
with an SYN-ACK, but without adding a fresh record to its SYN Queue. Instead, it does this only when the
SYN-ACK has been responded to (something that doesn’t happen in an SYN flood attack).
Another approach is an RST cookie, whereby the server will purposely send an incorrect response after it
receives the initiating SYN request. In the case of a genuine request, the server will receive an RST
packet that alerts the server that something has gone awry.
Still another approach involves micro-blocks, whereby the server allocates a micro-record for every SYN
request, rather than a complete connection object. This reduces straining resources in the event that
they have to deal with too many requests. Some of the newer versions of this micro-block approach can
allocate amounts as tiny as 16-bytes in response to incoming SYN objects.
One final approach to reducing the potentially devastating effect of SYN floods is called stack tweaking.
In this response, the timeout before a stack frees up might be reduced. Alternatively, it may selectively
choose to drop connections that are incoming.
SYN floods aren’t the only DDoS games in town
Source: tek-tools.com

Source: eetasia.com
As noted, SYN floods are far from the only kind of DDoS attack users can face here in 2020. DDoS attacks
can be extremely damaging, resulting in significant unwanted downtime and, potentially, financial and
reputational losses in the event that it causes organizations to be able to service customers.
DDoS attacks come in many forms, and each variant requires different approaches for dealing with
them. As these attacks become more widespread and virulent, it’s crucial that every organization is
properly protected against them. Unless you’re an authority on cybersecurity with a lot of time on your
hands to keep up to date, it’s a smart move to bring in the experts to help.
There are plenty of things to occupy your time running a business or other organization. Adding
“defending against all cyberattacks” may be one task too many.